Project Objectives
The project has six technical objectives: 1) Quantify impact of potential sophisticated attacks and identify major vulnerabilities in the IT/OT systems; 2) Develop a multi-channel robustification scheme to protect the communication infrastructure for utility and customer assets; 3) Extend situational awareness to the grid edge for attack detection; 4) Develop attack-resilient cooperative controls for distributed energy resources (DERs); 5) Recover and survive from attacks through distributed reconfiguration and resilient restoration; 6) Integrate novel technical solutions into the distributed and interoperable framework, OpenDSP. The technical solutions as security enhancements will be validated using the UCF’s microgrid control and security testbeds. Furthermore, they will be built into OpenDSP and demonstrated in utility field tests at two utility members.
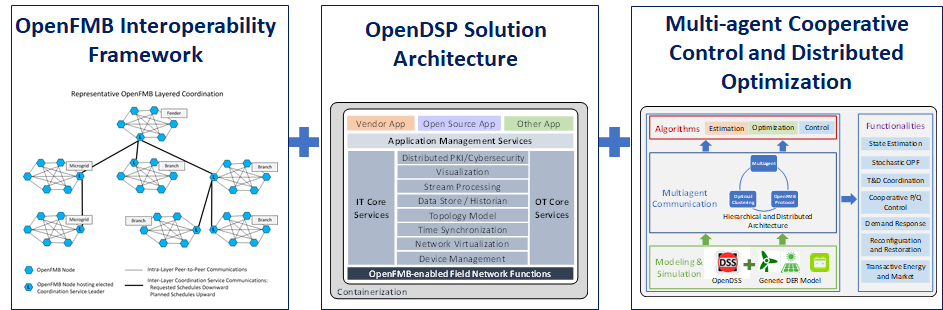
Project Innovations
The proposed project has four major innovations.
1) Container-enabled distributed intelligence and grid-edge interoperability: Distributed cooperative control and optimization will be advanced with security enhancements to provide attack-resilient response and recovery from attacks. The enhanced cybersecurity solutions leverage the OpenFMB interoperability framework, the OpenDSP solution architecture, the multi-agent cooperative control and distributed optimization solution algorithms, to enable trusted edge interoperability and scalability.
2) Multichannel solutions to extend enhanced situational awareness and event detection to the grid edge: A robust communication architecture through dynamic encoding using chaotic signals as watermark will be designed with multi-level overlapping topologies and virtual notes in hidden layers to protect critical IT/OT infrastructure, extend observability and attack detectability to the grid edge, and sustain system operation under attacks through dynamic defense with attack-resilient cooperative control.
3) Data-driven and learning-enabled schemes: This project will harness the time-series data of distributed nodes behavior and IT flows with white-listing, as well as a layered machine learning (ML) implementation, to provide an inference method for extended situational awareness at the grid edge, distributed behavior analytics (DBA) for attack detection, and device/system health prediction.
4) Distributed decision-making with probabilistic modeling and learning-enabled optimization: This project will model the uncertainty of sophisticated cyber-physical attacks and failures in vulnerability assessment and in adaptive and resilient IT/OT system recovery and survival, fully considering the complexity of interdependent cyber and physical systems.
These four major innovations lead to new security algorithms and schemes in each layer, all together to provide secure and resilient system operations. The enhanced cybersecurity solutions are transformative for utility adoption of distributed technologies and open-source platforms.
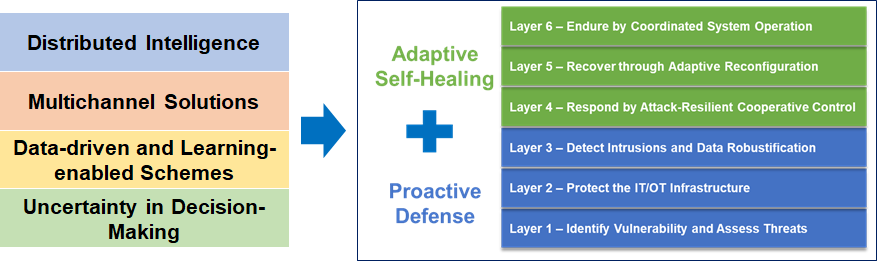
Project Tools
This project will develop IT/OT security solutions based on the framework shown in the following figure. The proposed multi-layered cybersecurity applications will be developed through integrating the key features of OpenDSP and MA-OpenDSS, enabling secure and resilient operations of both control centers and DERs.
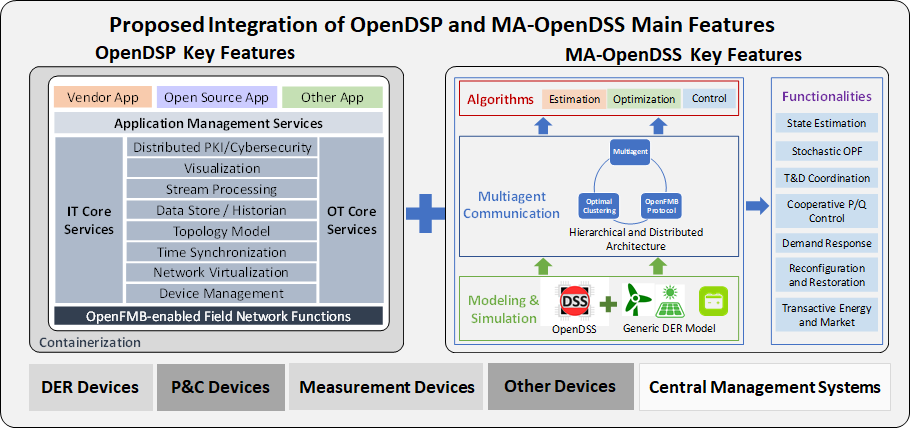
Project Outcomes
Outcomes for this project include new open-source functionalities and innovative algorithms of distributed intelligence that will be developed, tested through university testbeds, and integrated and validated in field demonstration. The expected project outcomes include IT/OT cybersecurity enhancement solutions in each of four major innovations, including distributed intelligence (attack-resilient control, distributed reconfiguration, adaptive and coordinated restoration), multichannel solutions (dynamic encoding with chaotic signals, multi-level state estimation, virtual notes and hidden layer), data-driven and learning-enabled schemes (inference for situational awareness, distributed behavior analytics, ML-based attack detection), and uncertainty in decision-making (probabilistic vulnerability assessment, resilience index-based recovery, device/system health prediction and correlation metrics); open-source software tools, including developed models and algorithms; testing and results on university testbeds and utility field demonstration; technology transfer to vendors and utility.