Research Projects Cover:



Research Projects Funded so far by:





Current Focus of Research (Ongoing)
[Research Project 6]
From SoC to SiP: Migration and Advancement of the Security Solutions for new Technologies
Significant signs of a slowdown of Moore’s law and Dennard scaling have pushed leading semiconductor companies toward advanced packaging with heterogeneous integration (HI) to stay away from the challenges of monolithic 2D ICs in more shrunk technology with higher complexity. It is consistent with the latest NIST Microelectronic and Advanced Packaging Technologies (MAPT) Roadmap initiative: “Advanced packaging, along with 3D monolithic and heterogeneous integration, will be the key enabler of the next microelectronic revolution. In fact, advanced packaging+3D is becoming the equivalent of the transistor of the 2D Moore’s Law era. This initiative closely aligns with SRC’s Decadal Plan, which stresses the urgency of increased research funding in this area”. It includes five crosscuts with leading academics, government agencies, and industry players involved. The fifth crosscut is the “security and privacy of HI”. Therefore, we initiated the concept of security of heterogeneous integration (SHI), in which we first explored how reliable and promising solutions in 2D SoCs can be extended to secure HI. By revisiting the trustworthiness of the system-in-package (SiP) supply chain, versus that of the SoC supply chain, we started to assess and engage possible trust validation and attack mitigation methodologies leading to establishing the fundamentals of end-to-end secure HI. We expand our research endeavor on this topic, which includes fault injection in HI, secure activation and HI-based locking, secure rule checking in HI, etc.

Selected Publications:
[Research Project 5]
Security by Construction: Early Stage Security-aware IC Design and Implementation
With the increasing demand for the latest technologies embedded in smart electronic devices, shorter time-to-market demands for SoCs, and complexity of smaller technology node sides, moving towards higher levels of abstraction (C/C++) via High-level Synthesis (HLS) enables designers to address such gaps (design complexity vs. demands). Hence, it is common to see designs start at the high level (e.g., C/C++) and then be translated to register transfer level (RTL) followed by gate level. HLS has paved the way for different entities to lower product development costs, verification efforts, and time-to-market. Also, many research endeavors have been directed to optimize and increase the efficiency of HLS for SoC design in terms of area, power, and performance. However, little effort has been put in place to comprehensively investigate potential security implications (information leakage, side-channel leakage, etc.) which could inadvertently be introduced by the HLS translation process. To address such concerns, we introduce secure design rule checking at the high-level design description, where we investigate different mechanisms, e.g., information flow tracking, path decoupling, security-aware resource utilization, etc., which aim to define and assess underlying (security-oriented) constraints for the design. By doing this, we can introduce security-aware SoC design and verification (at an early stage of the design).

Selected Publications:
[Research Project 4]
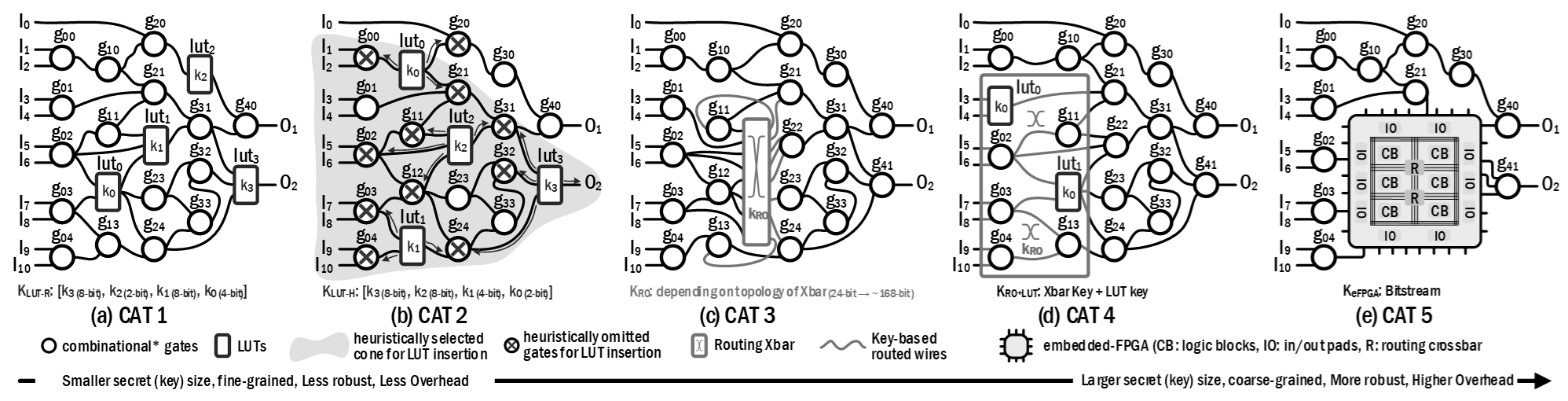
IC/IP Protection: Advanced Logic Locking and Secure Activation
Plunged in the globalization ocean of the IC supply chain, given the complexity and size of modern ICs/SoCs, the design teams will benefit from multiple 3rd parties throughout the IC supply chain. In such a globalized environment and with no reciprocal trust, numerous hardware security threats have emerged, such as IP piracy and IC overproduction. A solution against such threats is logic locking, which enables designers to lock designs at any stage of the IC supply chain where untrusted parties are involved (with post-manufacturing activation capability). Throughout this research direction, we try to answer some pivotal questions: (1) How should the design be modified for the purpose of locking to make it secure against untrusted/malicious activities? (2) How should the procedure of secure activation be done with no secret leakage? (3) How does the logic locking technique provide robustness against existing as well as new threat/attack models? (4) How does the logic locking technique respond to emerging technologies (e.g., probing)? (5) How could the design team transfer logic locking from one technology/environment to a new one? To address these concerns, we explore different locking techniques, different secure activation infrastructures, the EDA-adaptivity of the solutions, and their commercialization.
Previous Focus of Research (Previous)
[Research Project 3]
Forward Trust in IC Supply Chain: Enabling Secure Authentication and Provisioning
In the rapidly evolving landscape of IC development, hardware obfuscation (a.k.a. logic locking) has emerged as a crucial proactive safeguard against the growing supply chain threats. The importance of hardware obfuscation cannot be overstated, as it serves as a formidable barrier to untrusted entities seeking to compromise the integrity and security of ICs throughout the entire supply chain. However, as the saying goes, “no fortress is impenetrable“, while hardware obfuscation provides a robust layer of security within ICs, its implementation in isolation does not constitute a comprehensive solution, and simply integrating obfuscation within ICs and leaving the supply chain untouched exposes vulnerabilities that can be exploited by adversaries. The main aim of this project is to investigate and establish a full-fledged ecosystem of trust within the IC supply chain while maintaining the critical element of security, such as obfuscation. The project encompasses multiple key areas:
(1) Secure Design for Testability that focuses on IC design and testing, introducing measures to protect scan chains. This fortification ensures that the testing process itself is secure, reducing potential weaknesses that could be exploited by malicious actors; (2) Forward Implication for secure testing at any future steps of the IC supply chain; (3) Secure Communication via Primitives for Remote Activation in the realms of 3D design and IoT applications, in which we implement authenticated encryption for activation phase of hardware obfuscation against numerous forms of attacks, ranging from reverse engineering to probing; and (4) Uniqueness for Activation to make activation procedures unique and tamper-resistant against any form of hammering-oriented attack scenarios. These solutions are pivotal in curtailing the advantages that potential adversaries might gain when launching various attacks. With a multitude of applications, this project stands as a beacon of interest for the IC supply chain community.

[Research Project 2]
Towards Low Power Interconnection Architectures: Network-on-Chip Optimization
Network-on-Chip (NoC), as an integral component of modern computer systems, particularly in many-core and multi-core processors, provides a scalable and efficient communication infrastructure that enables high-speed data exchange between cores. Although super-beneficial in performance/throughput, efficiency in power and energy consumption is of critical importance in these architectures. As NoCs consist of numerous routers that can spend significant time in an idle state, addressing power efficiency in these routers is essential to reduce overall energy consumption and mitigate the impact of static power. This project focuses on reducing the power/energy consumption in these architectures by rectifying their main building components’ micro-architectures, e.g., alleviating leakage power in NoC routers. With a particular emphasis on the use of power-gating for NoC routers, we focus on the impact of deterministic routing algorithms to reduce the number of packets that encounter power-gated routers, maximizing idleness (being power-gated). We also focus on establishing dedicated paths (routing tables) between source-destination pairs to maximize router utilization. By optimizing routing algorithms, maximizing idleness for a set of routers (for more efficient power-gating), and efficiently managing powered-on and powered-off states, this project significantly improves statics power consumption and reduces latency, making NoC architectures more energy-efficient and practical for modern computing applications.

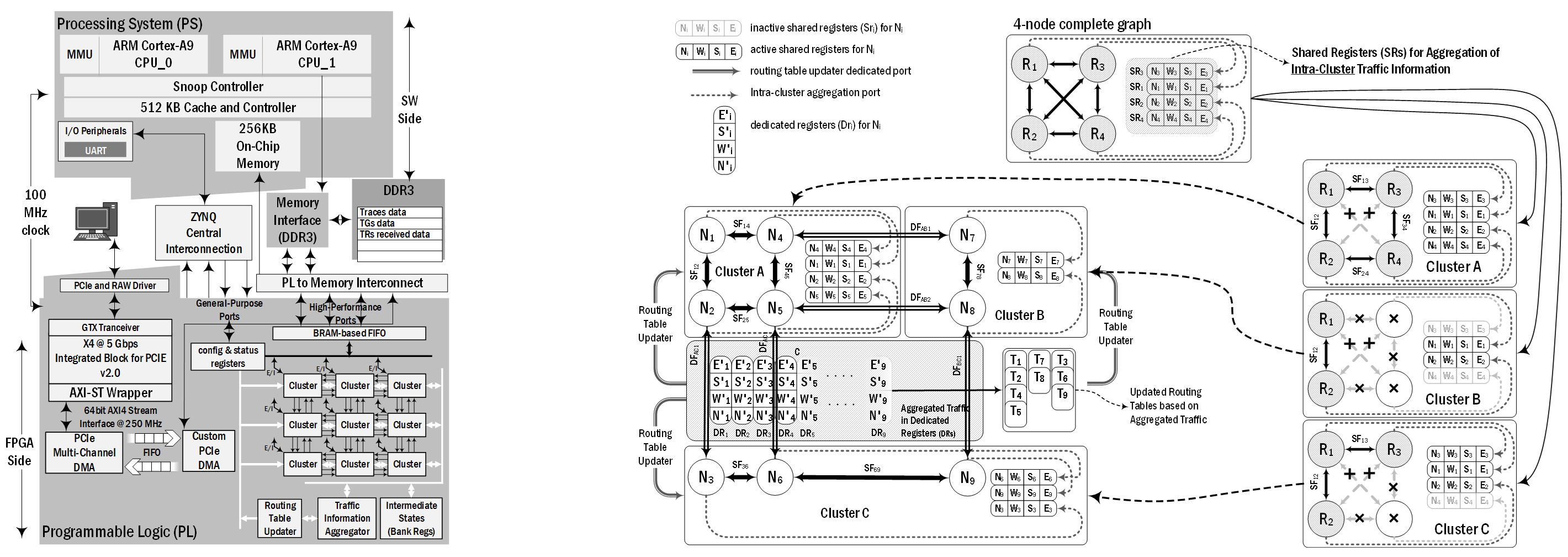
[Research Project 1]
FPGA-based Computer Architecture (Interconnection) Acceleration Solutions
FPGA-based acceleration in computer architecture has played a pivotal role in addressing the ever-increasing demand for faster and more efficient computing systems. Some applications are algorithm acceleration, high-performance computing, machine learning and AI on FPGA, network and cryptographic processing, etc. On the other side, multiprocessor systems-on-chips (MPSoCs) heavily rely on network-on-chip (NoC) as a fundamental interconnection platform, making it critical to have high-performance, cycle-accurate, and flexible simulation (emulation) tools. This project focuses on addressing this need by presenting innovative FPGA-based NoC simulation (emulation) solutions. The Significance of FPGA-Based acceleration and their inherent reconfigurability allows for the rapid prototyping of complex systems, such as NoCs, and enables the creation of cycle-accurate emulation engines. This project focuses on both reconfigurability and acceleration provided by FPGA for NoC emulators, by migrating non-computation-intensive components like Traffic Generators (TGs) and Traffic Receptors (TRs) to the software side (for better programmability), while keeping the computation-intensive components at the FPGA side, resulting in improvement in emulation performance. This project aims to contribute significantly to the optimization of NoC architectures and the realization of efficient application-specific solutions in the ever-evolving landscape of computer architecture.